1. Introduction
Cisco AnyConnect is a VPN solution from Cisco Systems. It can use either a Cisco ASA Firewall, or Cisco Identity Service Engine (ISE) as its authentication and authorization mechanism. Trusona can integrate with both a Cisco ASA or Cisco ISE using the Trusona RADIUS Appliance. This guide will walk through integrating Trusona with both Cisco ASA and Cisco ISE.
2. Integrating with Cisco ISE
The Trusona RADIUS Appliance can integrate with Cisco’s Identity Services Engine (ISE) as an External Identity Source.
- Go to Administration > Identity Management > External Identity Sources
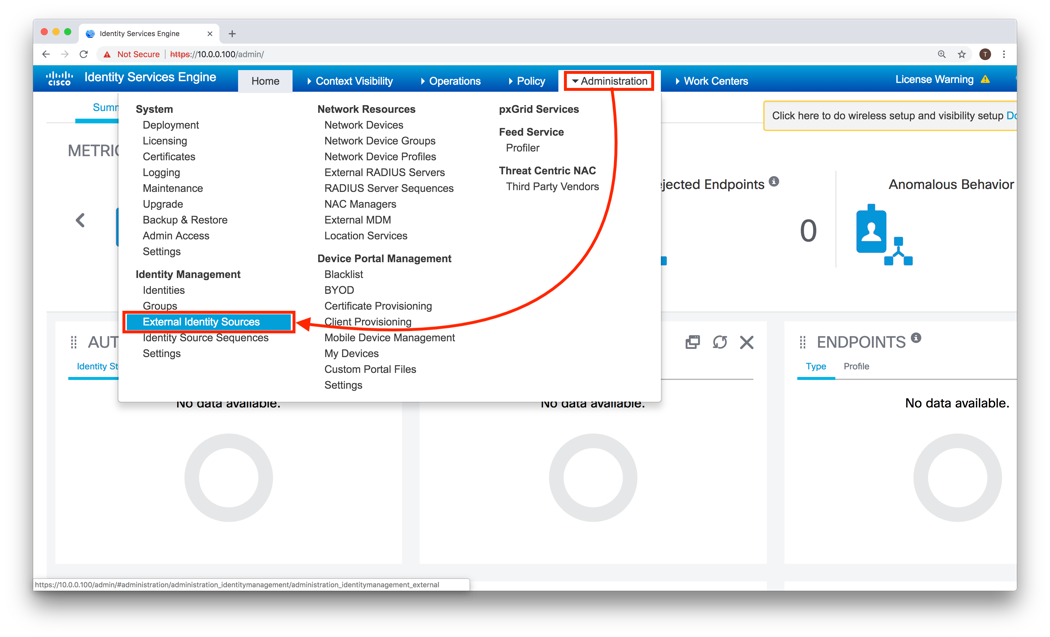
- On the left hand side select RADIUS Token
- Click Add
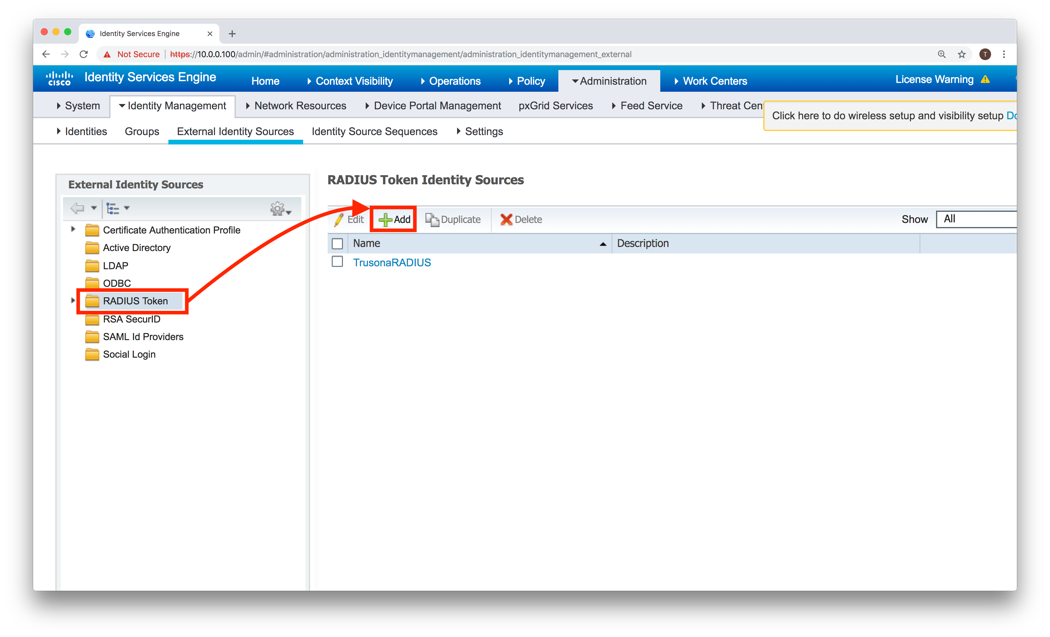
- Under General, enter a Name and Optional Description
- Click on the Connection tab
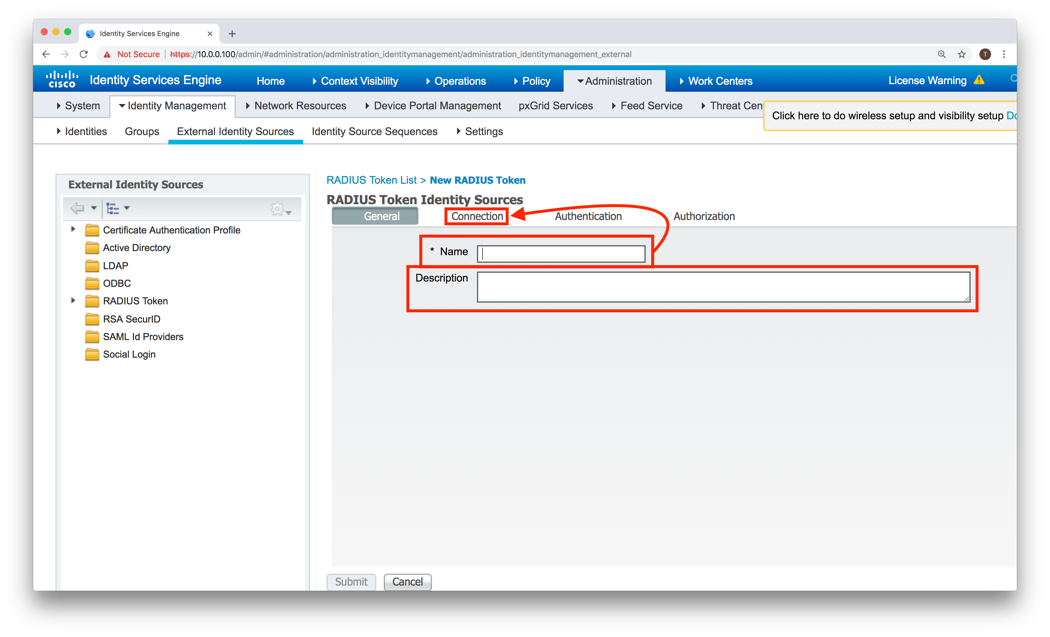
-
Complete the Primary Server section using the following information
- Host IP is the RADIUS Appliance’s IP Address
- Shared Secret is the RADIUS Secret configured on the appliance
- Server Timeout should be a number larger than Trusonafication Timeout configured in the RADIUS Appliance
- Connection attempts
-
Click Submit to save
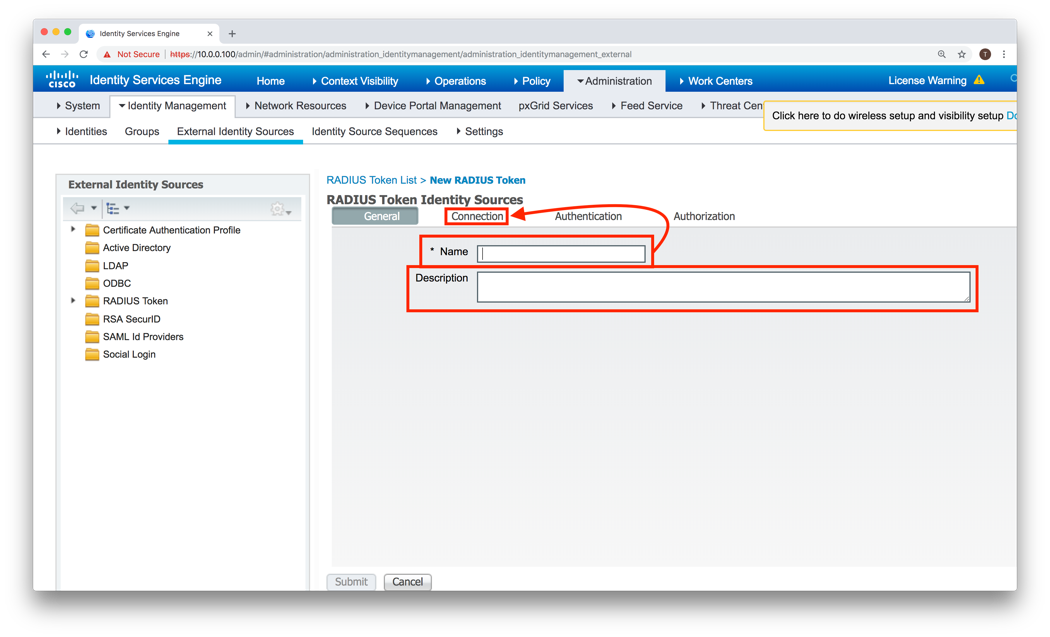
Now that the RADIUS Appliance is an External Identity Source, it can be used in Policies to authenticate users with Trusona using their email addresses.
3. Integrating with Cisco ASA
The Trusona RADIUS Appliance can be used as a AAA Server for Cisco ASA appliances. AAA Servers can be used for console access and/or VPN access on Cisco ASAs. The following configuration can be used to add the appliance as a AAA Server:
hostname(config)# aaa-server trusona-radius protocol radius
hostname(config)# aaa-server trusona-radius (inside) host 10.0.0.100
hostname(config-aaa-server-group)# timeout 65
hostname(config-aaa-server-group)# key radius-secret
hostname(config-aaa-server-group)# authentication-port 1812
hostname(config-aaa-server-group)# accounting-port 1813
In the above example, 10.0.0.100 is the IP address of the RADIUS appliance, and the configured RADIUS Secret is ‘radius-secret’ You can then apply the aaa-server to a tunnel-group for authorization:
hostname(config)# tunnel-group vpngroup
hostname(config)# tunnel-group vpngroup general-attributes
hostname(config-tunnel-general)# authentication-server-group trusona-radius
Or you could use it for console access:
hostname(config)# aaa authentication ssh console trusona-radius LOCAL