1. Prerequisites
Before proceeding, ensure that you have the following steps completed:
- Admin access to Okta Cloud IAM.
- Have admin access to the Trusona Dashboard. If your company does not have an account, visit the Trusona Dashboard to create one. Otherwise, consult with the owner of your company’s Trusona Dashboard account in order to create the integration.
2. Getting Started
2.1. Log into the Okta admin portal
If you are logged into the developer portal by default than select the dropdown that reads Developer Console and click Classic UI
If you see this page, click on the Admin button.


2.2. Create API token
Navigate to Security > API and then click the Create Token button.
Copy your API token (Token Value) and save it somewhere safe. You will be using it in later steps


2.3. Create a group
Navigate to Directory > Groups > click Add Group and create a name and a description.
- Name the group Trusona
- Provide a group description
- Click Add Group
This group is used to prevent users, who are using Trusona for passwordless login, from being prompted for an additional second factor of authentication.
You don’t need to maintain the membership of this group. Group membership is automatically managed by Trusona via the Okta API. Do not add any members to the group.

2.4. Navigating the dashboard
From the Trusona Integration dashboard, navigate to Okta Integrations & click on Create Okta Integration.
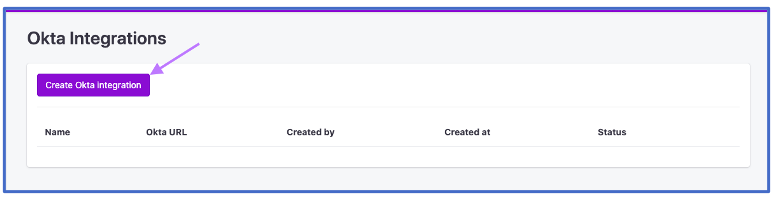
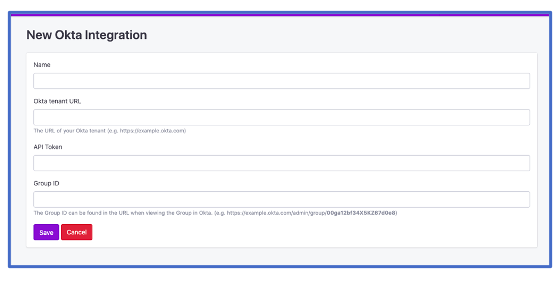
2.5. Inputing Data
4 different input fields will be shown.
-
Name
-
Okta Tenant URL
- This will look similar to https://example.okta.com.
-
API Token
- The value from the token you made in Step 2.
-
Group ID
- This is the value from the URL you copied in Step 3.
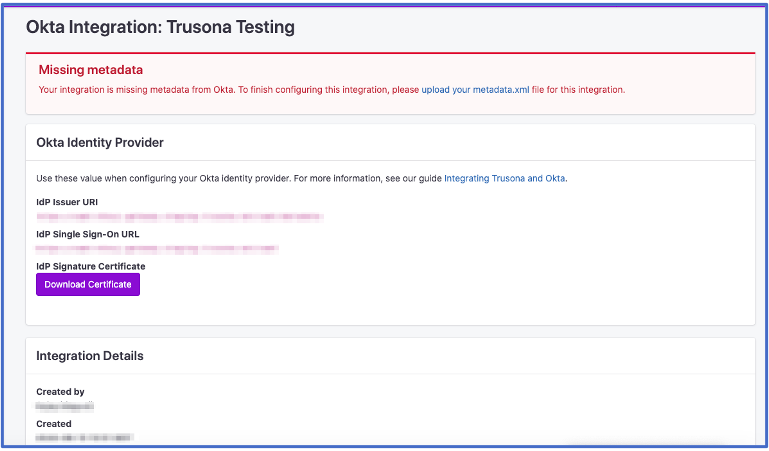
2.6. Accessing generated data
Click on Save after entering all relevant information. Trusona will generate data that you will use in the Okta platform. Don’t worry about the warning message regarding “Missing metadata“ for now.
3. Create an Identity Provider
Navigate to Security > Identity Providers > Click Add Identity Provider > Click SAML 2.0 IdP.

Note: If the “Add Identity Provider” button does not have a drop down then click “Add Identity Provider” and continue with the steps below.
Complete the form to add the new SAML IdP using the information below:
3.1. General Settings
| Field | Value | Instructions |
|---|---|---|
| Name | Trusona |
3.2. Authentication Settings
| Field | Value |
|---|---|
| IdP Username | idpuser.subjectNameId |
| Filter | Unchecked |
| Match against | Okta Username |
| If no match found | Create new user (JIT) |
3.3. JIT Settings
| Field | Value | Instructions |
|---|---|---|
| Profile Master | Unchecked | |
| Group Assignment | Assign to specific groups | |
| Specific Groups | Your Group Name | Enter the group name created in step 5. |
| If no match found | Create new user (JIT) |
3.4. SAML Protocol Settings
Click the ‘View’ button on the Okta integration in your Trusona Dashboard to view your IdP Issuer URL, IdP Single Sign-On URL, and Signature Certificate.
| Field | Value | Instructions |
|---|---|---|
| IdP Issuer URI | https://gateway.trusona.net/saml/metadata |
|
| IdP Single Sign-On URL | https://<YOUR ORIGIN URL>/saml |
This is unique to your integration with Trusona. and will look something like https://example.gateway.trusona.net/saml
|
| IdP Signature Certificate | Download the Signature Certificate by clicking the ‘View’ button on the Trusona Dashboard and clicking ‘Download Certificate’ |
Once the information in the tables above has been entered into the form, click the Add identity provider button to continue.
4. Add Origin
Navigate to Security > API > Trusted Origins and click the Add Origin button.
- Name your Origin Trusona.
- To create your Origin url, copy your IDP Single Sign-On from the Okta integration in the Trusona Dashboard then delete the
https://and/saml. Example:example.gateway.trusona.net - Enter you newly created Origin URL.
- Check both CORS and Redirect checkboxes.
5. Create new Sign-On policy
5.1. Navigate to “Security” > “Okta Sign-on Policy”
To create the new policy, click the Add New Okta Sign-on Policy button.
- Enter TrusonaUsers for the Policy Name.
- Choose a meaningful description for the Policy Description.
- Add the group you created in step 5 in the Assign to Groups section.
- Click Create Policy and Add Rule.
- Rule Name: Name rule (This rule allows users to authenticate from anywhere).
- Ensure that Require secondary factor is unchecked. (If “Require secondary factor” is checked, users may see unnecessary 2FA prompts after using Trusona to login to Okta.)
- After creating a rule make sure the new rule is activated.

6. Create Routing Rule
Note: Do not move onto step 10 until you have completed step 9. Otherwise you may be locked out of your account.
- Navigate to Security > Identity Providers > Routing Rules.
- Click the Adding Routing Rule button.
- Match the fields below.
- Click Create Rule.

| Field | Value |
|---|---|
| Rule Name | Trusona |
| User’s IP is | Anywhere |
| User’s device platform | Any device |
| User is accessing | Any application |
| User matches | Anything |
| Use this identity provider | Trusona |
Trusona recommends that this newly created routing rule be placed above existing routing rules. This ensures that users are redirected to the Trusona IdP for authentication. Your specific implementation and/or deployment needs may require the rule to be placed somewhere other than first in the list.
7. Create a Trusona Registration application
The Trusona Registration application helps your users link their Okta account to their Trusona Account. This process guarantees that users are identified by the Trusona IdP with a known and valid Okta identifier. All users that intend to use Trusona to login with Okta should complete the registration process described below before attempting to use Trusona to login to Okta.
7.1. General Settings
- Applications > Applications > Add Application.
- Click Create New App.
- Choose the SAML 2.0 optioon.
- Click Create.
- Click Next.


| Field | Value |
|---|---|
| App name | Trusona |
| App logo | Trusona logo |
| App visibility | Unchecked |
7.2. Configure SAML
- Navigate to the Okta integration in the Trusona Dashboard -> Click Actions -> Show -> Under “Trusona Registration Application”, copy the IdP Single Sign-on URL. The url will end in
/registrations. Example:https://example.gateway.trusona.net**/registrations - In Okta, re-open the Trusona application and enter the IdP Single Sign-On URL.
- Check on “Use this for Recipient URL and Destination URL”.
- Audience URL (SP Entity ID): Enter
https://gateway.trusona.net/saml/metadata - Click Next.
7.3. Upload the Okta X.509 Certificate to Trusona
- In Okta, Applications -> Applications -> Trusona -> Sign On -> Click View Setup Instructions under “SAML 2.0 is not configure until you complete the setup instructions” prompt -> Scroll down to X.509 Certificate -> Click Download Certificate.
- Go to the Trusona Dashboard -> On the left hand side, click on Generic SAML integration and the Okta integration you created will be listed.
- Select Actions -> Edit -> Under Certificate click Choose File -> Upload the X.509 Okta Certificate -> Click Save in the bottom left corner.
7.4. Feedback
- Click the radio button “I’m an Okta customer adding an internal app”.
- Click Finish.

7.5. Create an Assignment
Within the new Trusona application > Assignment > Assign.
- Assign to Groups.
- Select Everyone.
- Click Assign.
- Click Done.


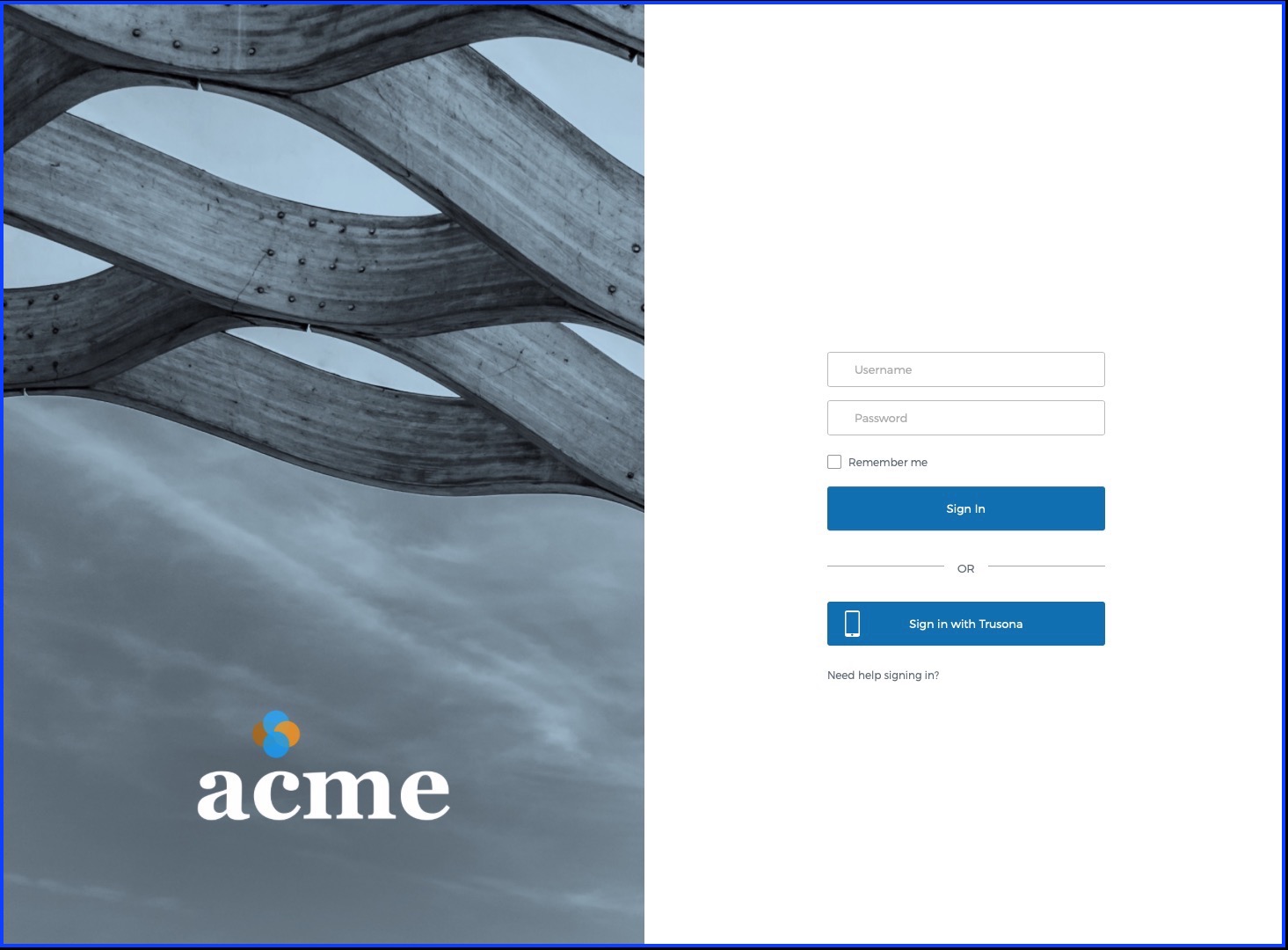
8. Customizing your Trusona experience
The Trusona Gateway (pictured below) includes default styling that will be familiar to your users using the Trusona App.
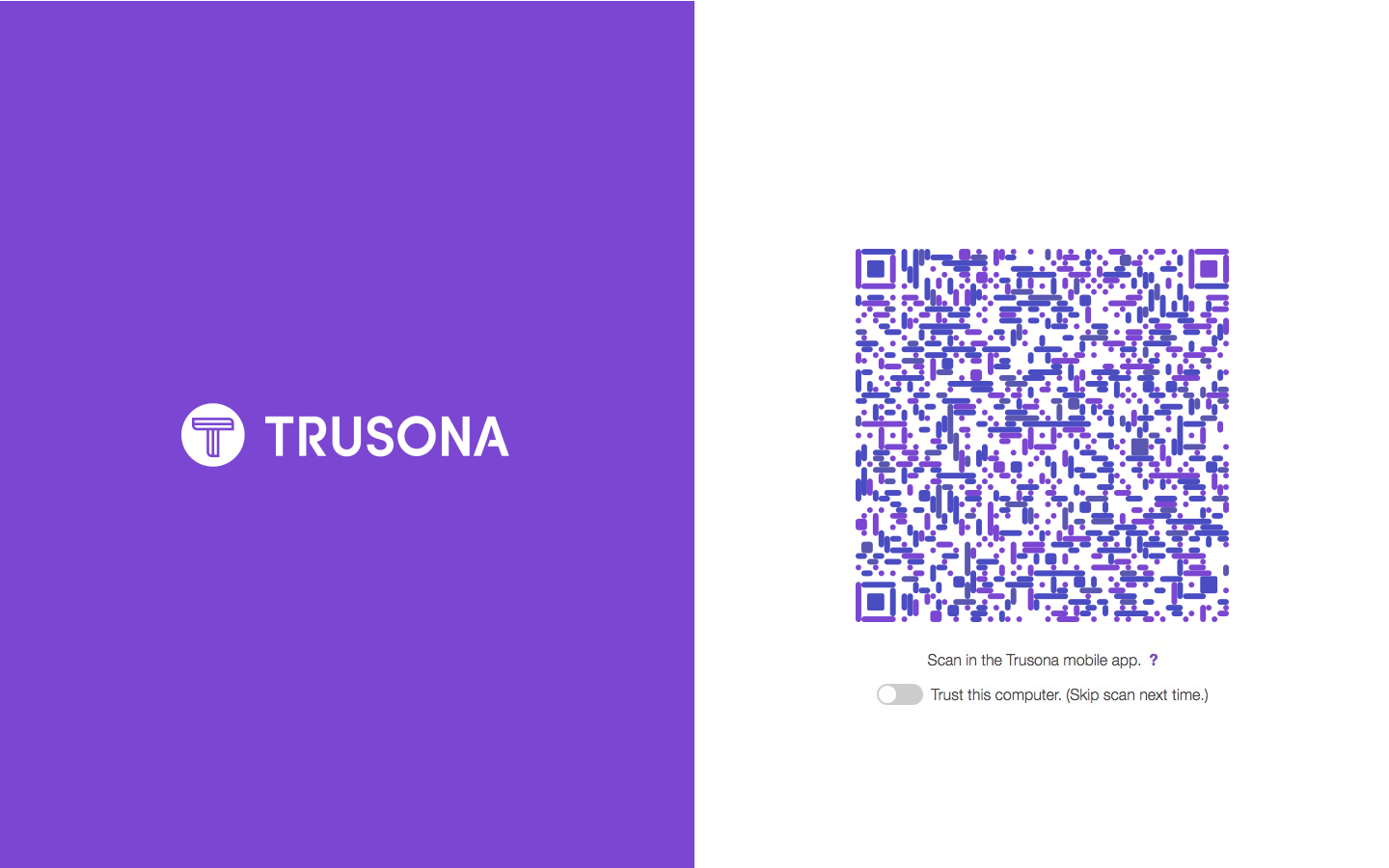
Optionally, it’s possible to provide a custom branded experience for your users including things like:
- A custom vanity URL
- Custom secure QR code colors
- Your company logo and colors
In order for Trusona to create your custom gateway you need to provide to Trusona hex values and images for the following:
8.1. Provide images
- Hero image: 1440 x 1800 px
- Logo image: 500 x 500 px
8.2. Provide hex values
- Animated dot color: this is the color dots that animate
- List of QR colors: multiples of the same color will appear more (provide 2 hex values)
- Link color: also changes the Okta widget button colors
- Text color:
- Background color: affects background behind the QR, usually we just do pure white (#FFFFFF)

9. Okta Identifier Registration
Users who intend to use Trusona to login to Okta must complete these required one-time steps.
- Download and install the Trusona App.
- Register in the Trusona App.
- Login to Okta using their existing username and password.
- Find, and click on, the Trusona application “chiclet” created in Step 10.
- Scan the QR code with the Trusona App.
- Accept and complete the Trusonafication.
The user’s Okta identifier has now been linked to their Trusona account and they are now ready to use Trusona to login with Okta.
Please see Integrating Trusona and Okta SCIM for SCIM provisioning.