1. Install and configure the Trusona Mac Setup app
(1) Download the Trusona Mac Setup app to install the application, drag it to your Applications folder.
(2) Launch the Trusona Mac Setup app. If this is the first time you are launching the app, you will be prompted to enter an administrator password so the app can install a Privilege Helper tool. This tool allows the setup app to store your credentials safely and modify the authentication process used to login to your computer.
A Get Started window will appear.
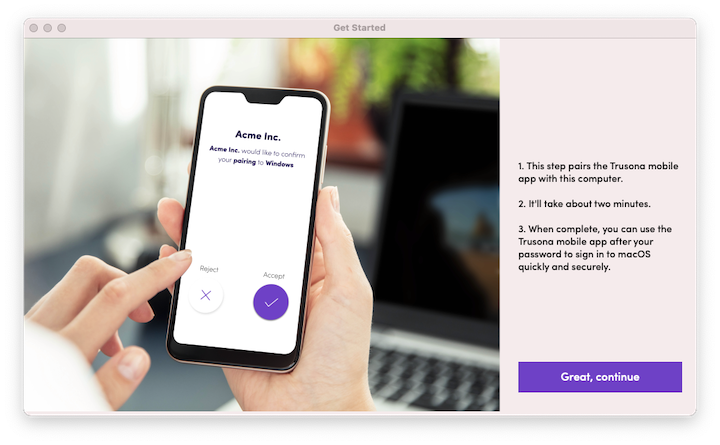
(3) Open the Preferences window (Trusona Mac Setup > Preferences). If your Trusona SDK credentials are already filled in, you can skip ahead to section 2 Getting Started.
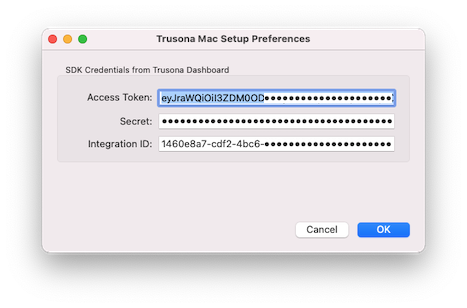
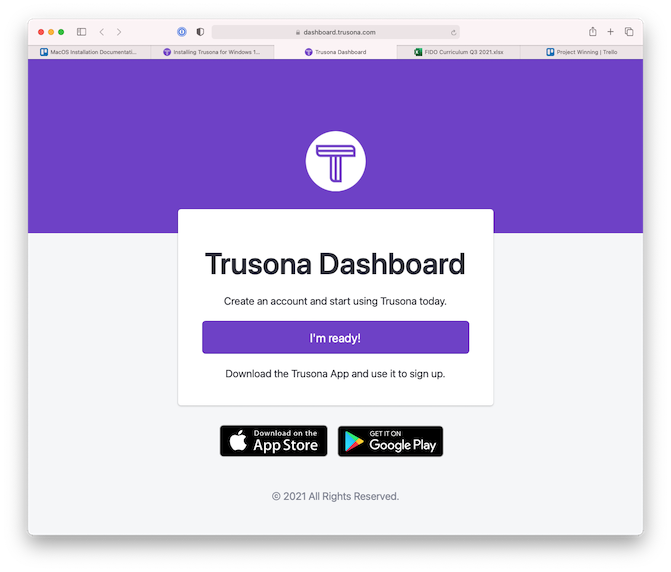
(4) If the SDK credentials are not already filled in as above, you will need to obtain them from the Trusona Dashboard. Navigate and Log in to the Trusona Dashboard - https://dashboard.trusona.com.
(5) On the dashboard home page, click on “SDK Credentials” on the left navigation pane and then click “Create Server Credentials”.
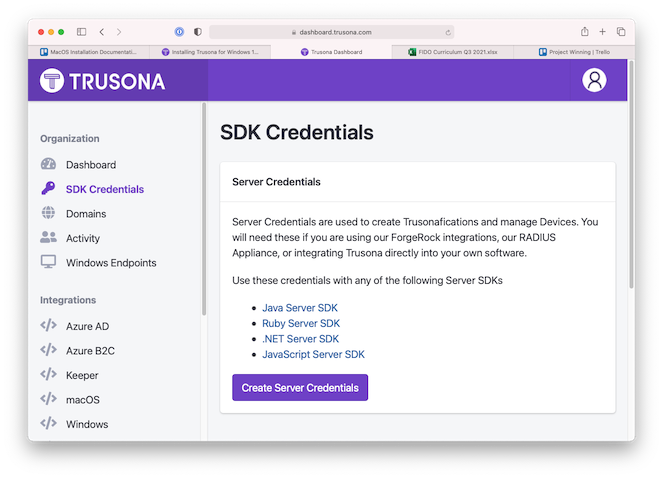
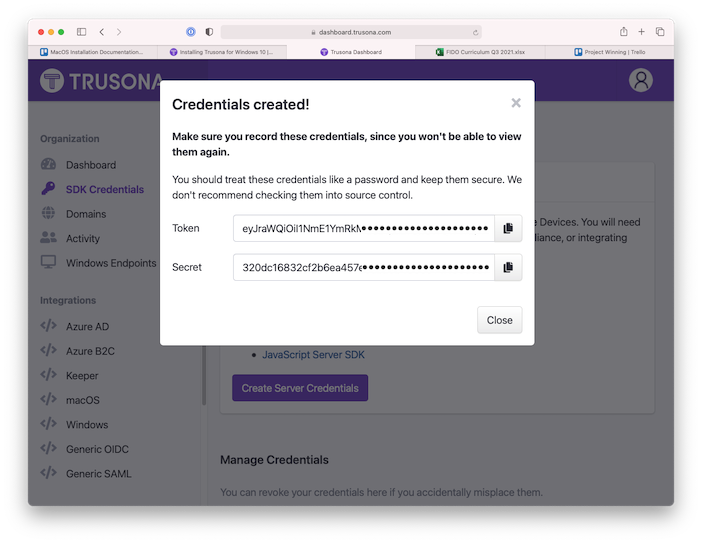
(6) Copy and paste these credentials into the corresponding fields of the Trusona Mac Setup preferences window. Once you navigate away from this page, these SDK credentials will not be shown again. You can copy them to a safe place (recommended), or create new ones if needed.
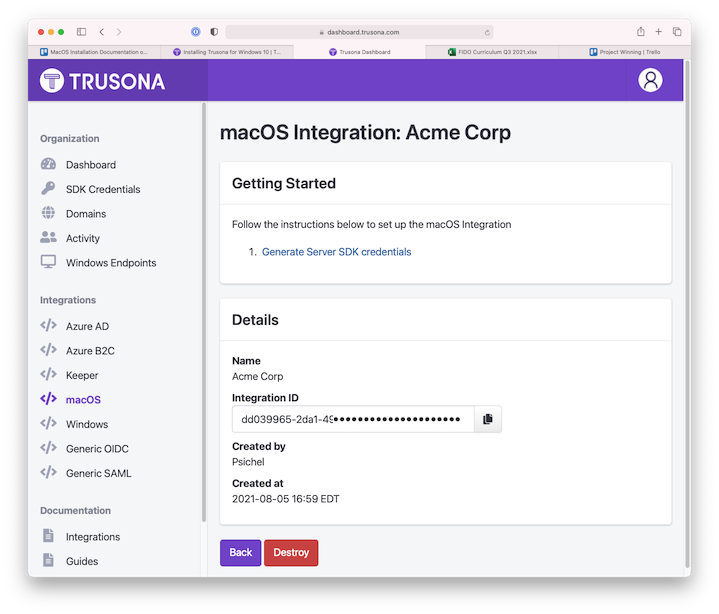
(7) Under the “Integration” subheading on the left, click on “macOS”. Press “Create macOS integration” and give your integration a name.
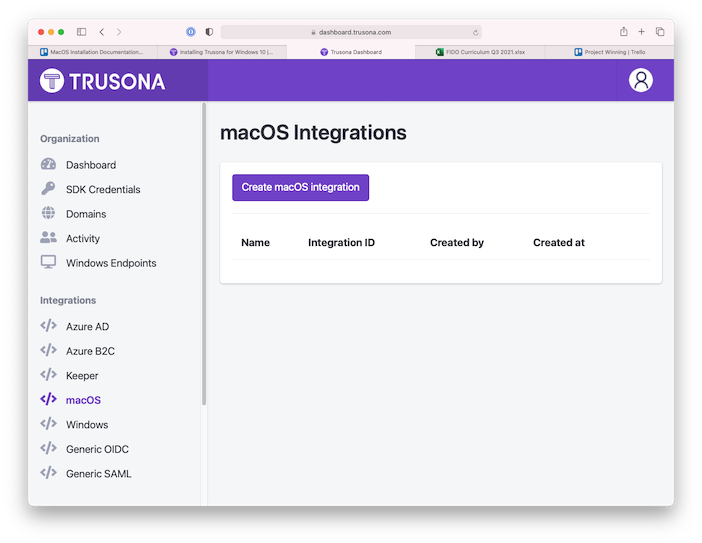
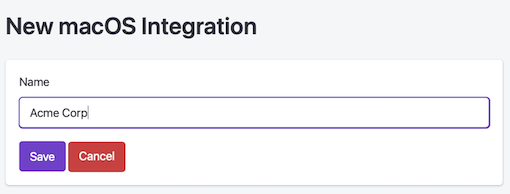
(8) Copy and paste the Integration ID to the corresponding field in the Trusona Mac Setup preferences window.
(9) Click OK in the Preferences window to save your credentials and close the window.
2. Getting Started
In this section you will associate your smartphone with your Mac and do a test login.
(1) Click in the Get Started window if it is visible or navigate to Trusona Mac Setup > Help > Get Started

(2) Follow the on-screen instructions to step through setting up the mobile app and pairing your smartphone with your computer. You may have already setup the Trusona mobile app and account previously.
(3) After you have “paired” your phone with your computer, complete the practice login. This ensures you will be able to log in once you enable Trusona authentication.
(4) The last step of the Get Started walk-through is to enable Trusona authentication.
(5) To test that you can authenticate, navigate to System Preferences > Security & Privacy and then click on the lock (lower left) to authorize making changes. You should be prompted for your password followed by a request to approve in the Trusona Mobile App.
(6) After you enable Trusona, you will need to logout and log back in once before the Lock Screen will require Trusona authentication. MacOS doesn’t see the change to the Lock Screen configuration until the next time you login.
(7) If you are only installing Trusona on this one computer, you are done. You can quit Trusona Mac Setup.
If you update to a newer version of the software, the Privilege Helper may need to be updated to match the corresponding version of Trusona Mac Setup.
3. Mass Deployment of Trusona macOS App using Jamf Pro
Prerequisites:
- Trusona SDK Credentials as described above (section 1.1).
- Jamf Pro
- Composer app
- Trusona Mac Setup app
- Mac test machine
3.1. Create a “credential.json” file
To setup Trusona authentication for additional users, you will need to create a small file containing SDK credentials that can be placed on each computer. The file must be named credential.json and will be placed at: /Library/Application Support/Trusona/. The format of the file which you can edit with your SDK credentials is shown below:
{
"mac_key" : "SECRET_FROM_DASHBOARD",
"api_host" : "https:\/\/api.trusona.net",
"access_token" : "TOKEN_FROM_DASHBOARD",
"integration_id" : "INTEGRATION_ID_FROM_DASHBOARD"
}
3.2. Create the package
a. Start with a clean install of macOS on your Apple test computer
b. Install Composer on test machine (the Composer app is included with your Jamf Pro license, please see user guide for details: https://www.jamf.com/resources/product-documentation/composer-user-guide/)
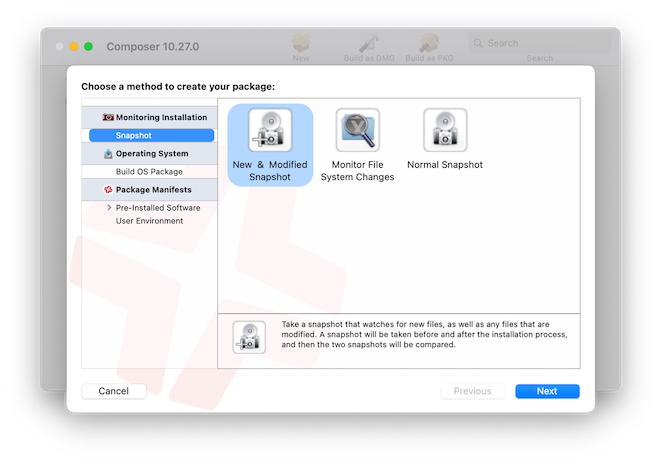
c. Create a new “New and Modified Snapshot” in Composer:
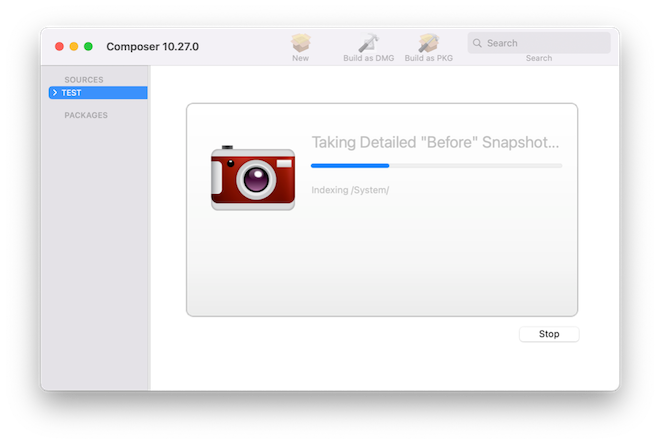
d. Wait until “Before Snapshot” is complete:
e. Place the Trusona Mac Setup app in the root Applications folder (ensure this is the root application folder and NOT the user application folder or else the app will only be available to the currently logged in user).
f. Place the credential.json file you created above at: /Library/Application Support/Trusona/
g. Finish the snapshot process and select the “Create as DMG” option.
h. Set Owner to root and Group to wheel:

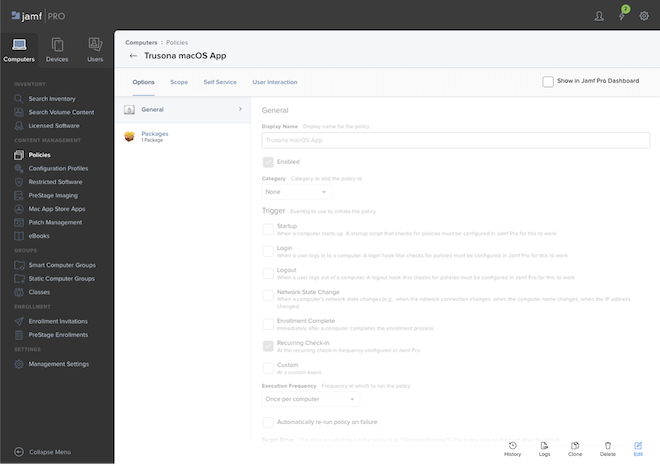
3.3. Deploy via Jamf Pro
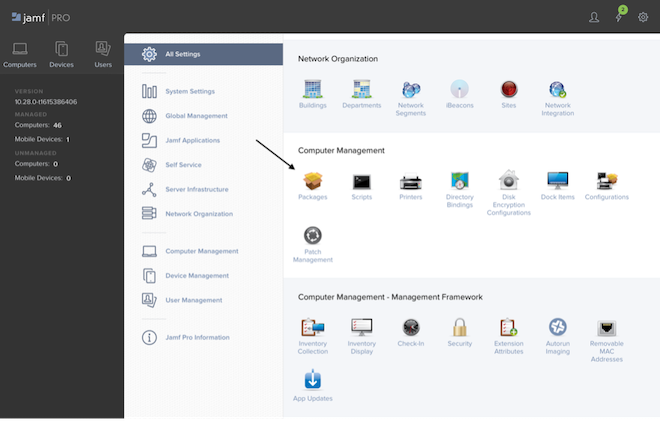
i. Upload the package created in step one to the Jamf Pro repository under All Settings/Computer Management:
j. Create a new Computer policy
k. Configure the Packages blade and select the newly created package
l. Define your scope
m. Set the Trigger to “Recurring Check-In”
n. Set the Execution Frequency to “Once per computer”
o. Save the policy
4. Mass Deployment of Trusona macOS App using Kandji
Prerequisites:
- Trusona SDK Credentials as described above (section 1.1)
- Kandji
- Trusona Mac Setup app
- Mac test machine
4.1. Create a “credential.json” file
To setup Trusona authentication for additional users, you will need to create a small file containing SDK credentials that can be placed on each computer. The file must be named credential.json and will be placed at: /Library/Application Support/Trusona/. The format of the file which you can edit with your SDK credentials is shown below:
{
"mac_key" : "SECRET_FROM_DASHBOARD",
"api_host" : "https:\/\/api.trusona.net",
"access_token" : "TOKEN_FROM_DASHBOARD",
"integration_id" : "INTEGRATION_ID_FROM_DASHBOARD"
}
4.2. Create the custom application for the Trusona installer
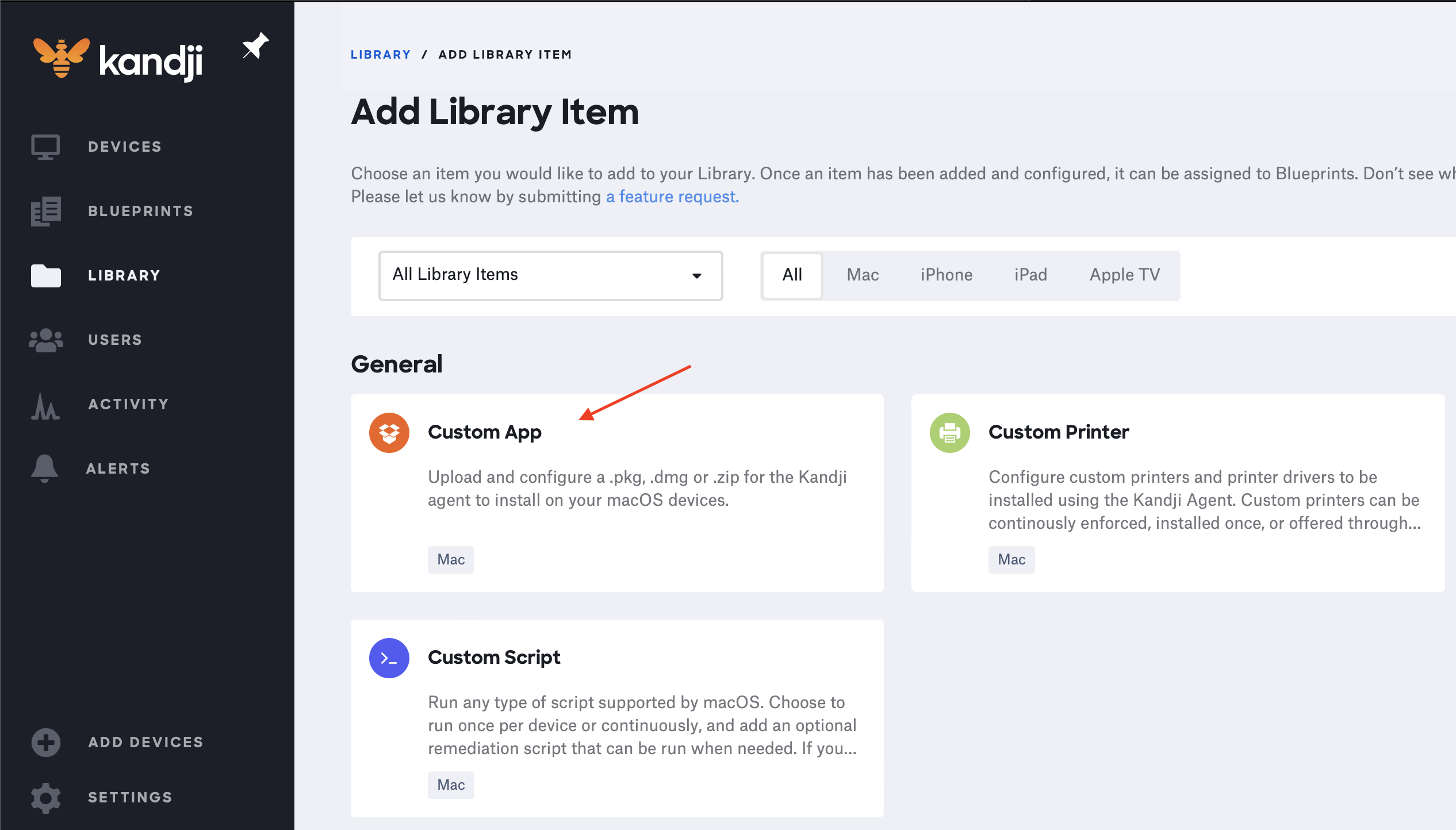
(1) From the Kandji admin portal, click on “Library” in the left-hand menu
(2) Click on the blue “Add new” button in the upper right-hand corner
(3) Under “General”, click “Custom App”
(4) Click the blue “Add & Configure” button
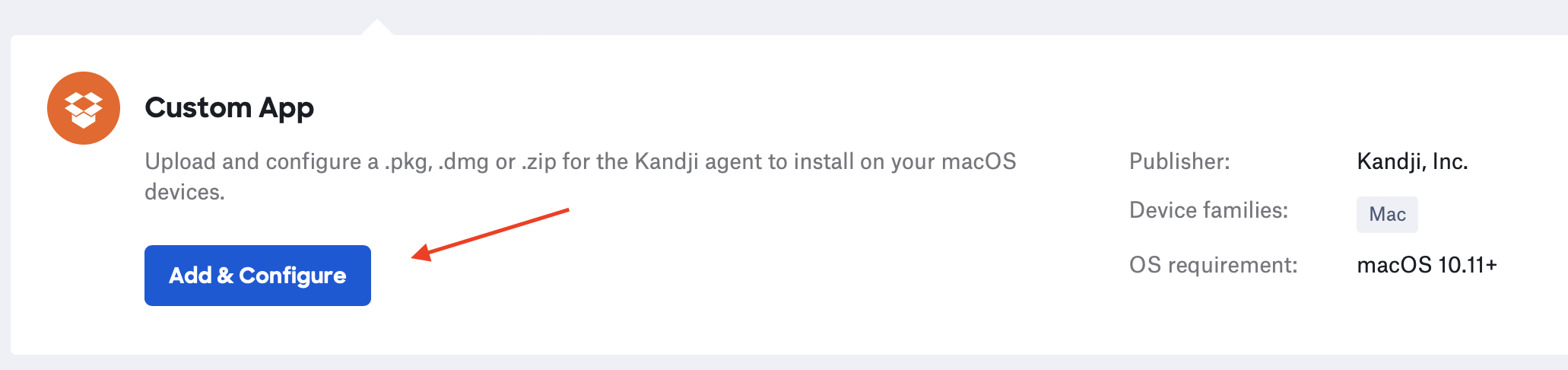
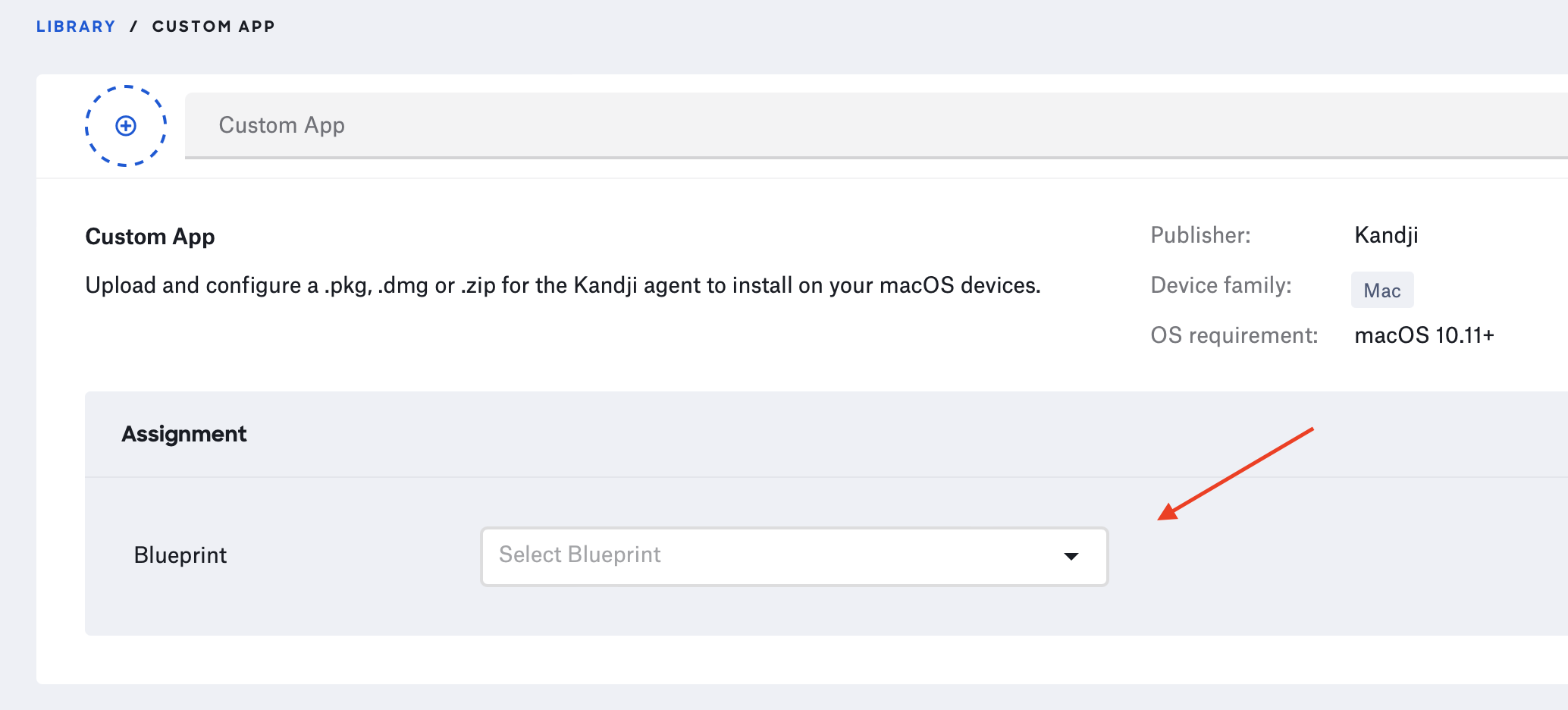
(5) Under the “Assignment” section, select the Blueprint that is assigned to the device you want to install Trusona on
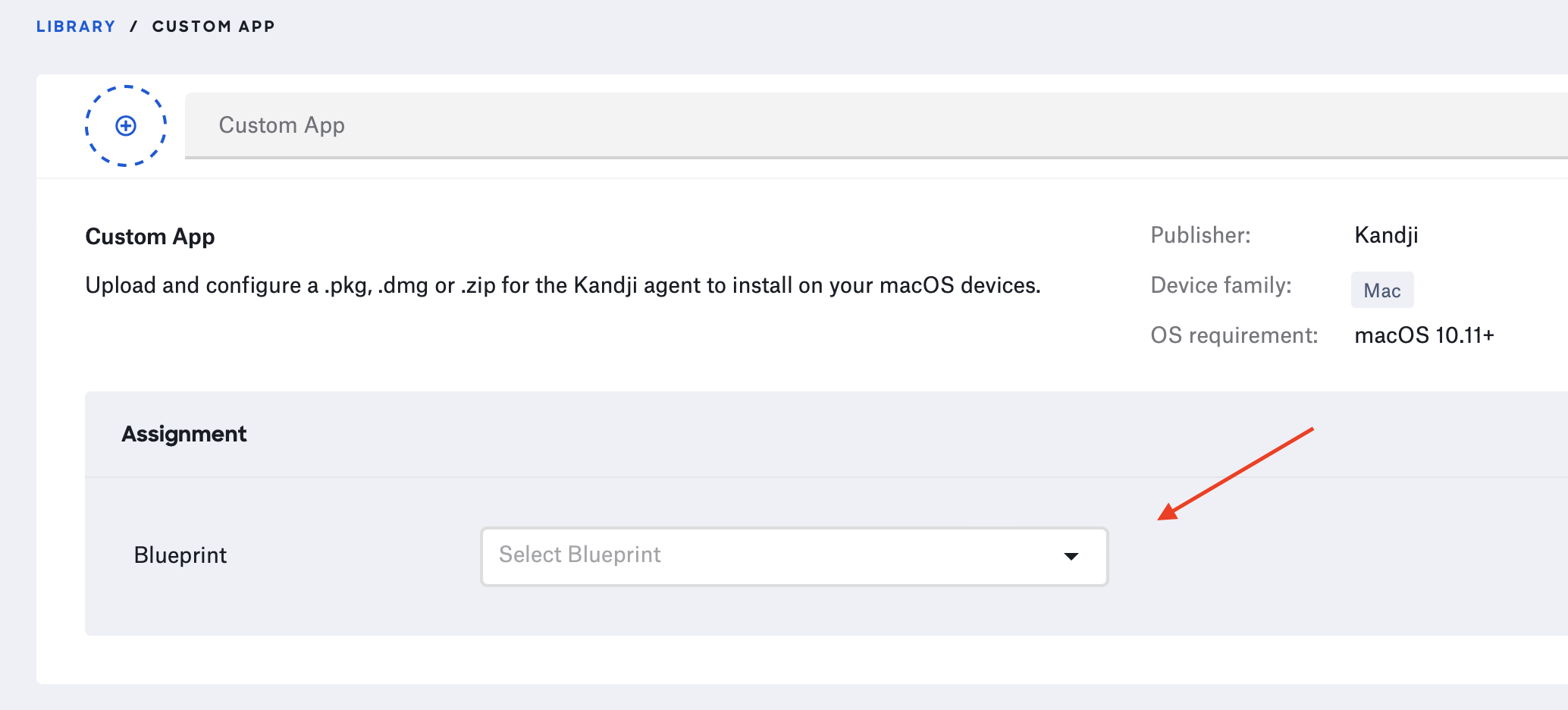
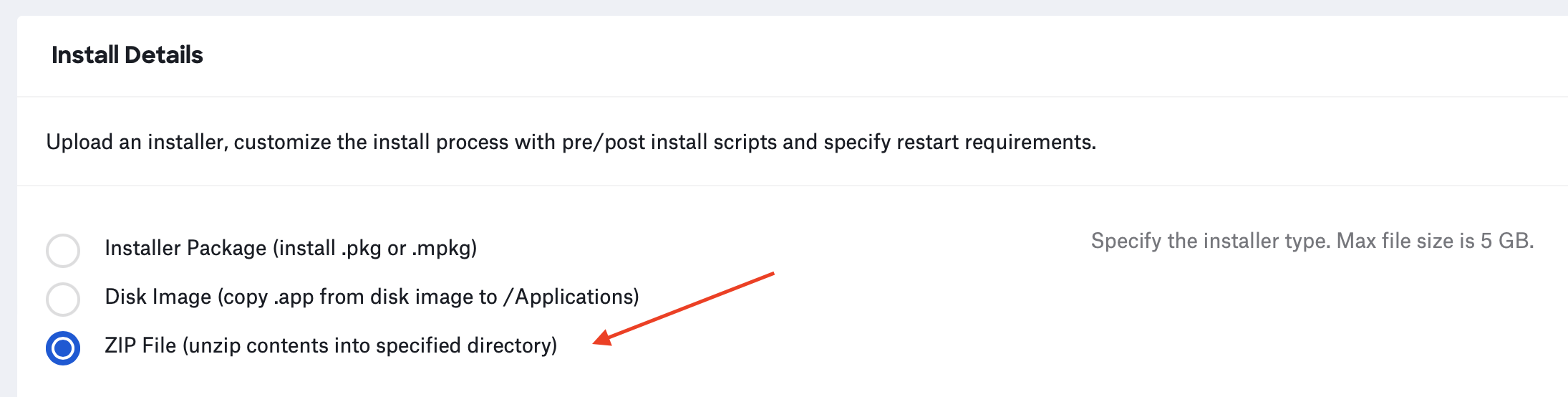
(6) Scroll down to “Install Details” and select the “ZIP File” radio button
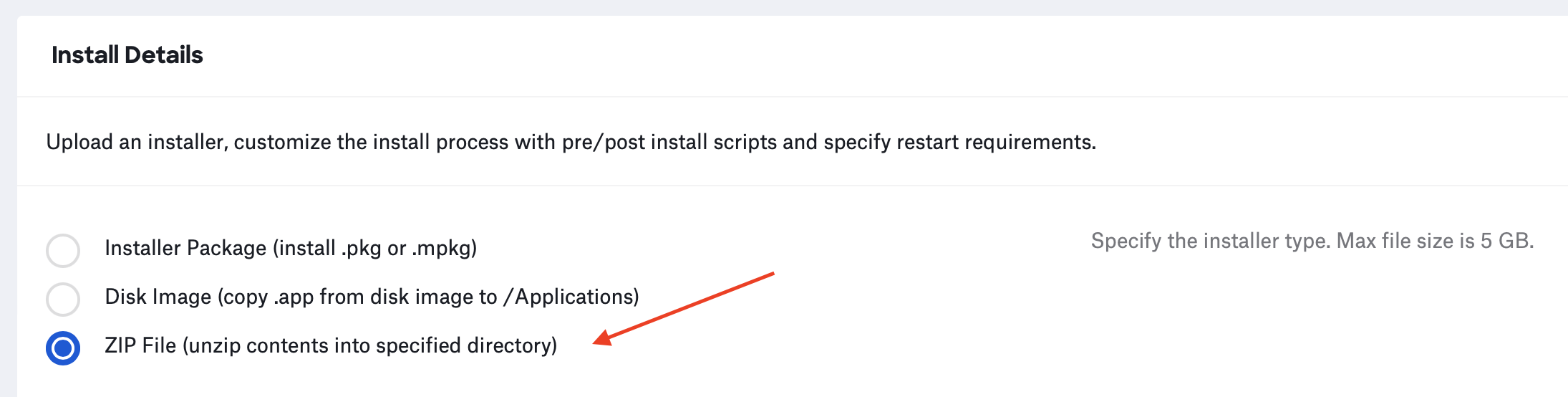
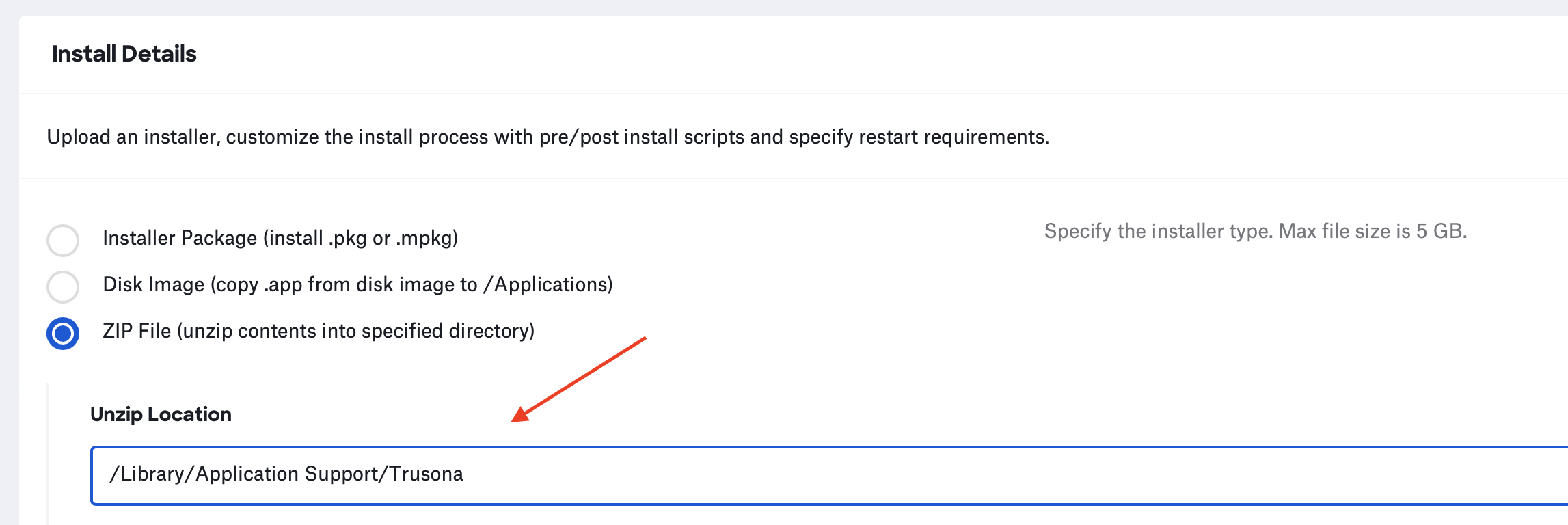
(7) In the “Unzip Location” text field enter “/Applications/”
(8) Drag and drop the Trusona app to the upload section under “ZIP File”
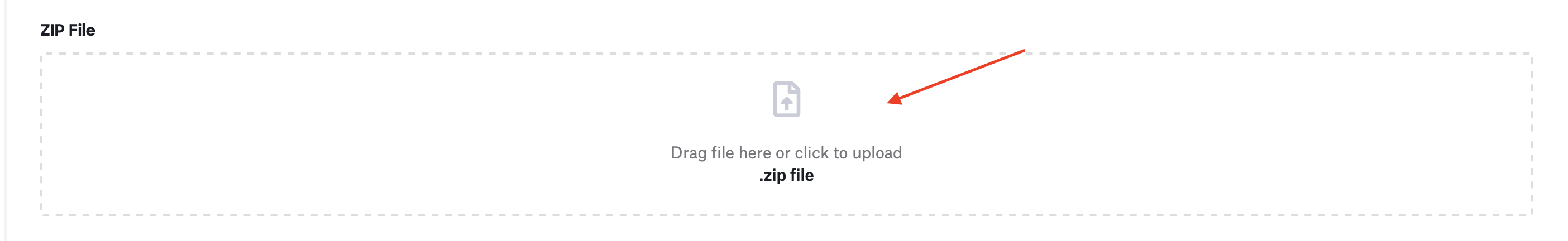
(9) Click the blue “Save” button in the bottom right-hand corner
4.3. Create the custom application for the credential.json file
(1) Click on “Library” from the left-hand menu
(2) Click on the blue “Add new” button in the upper right-hand corner
(3) Under “General”, click “Custom App”
(4) Click the blue “Add & Configure” button
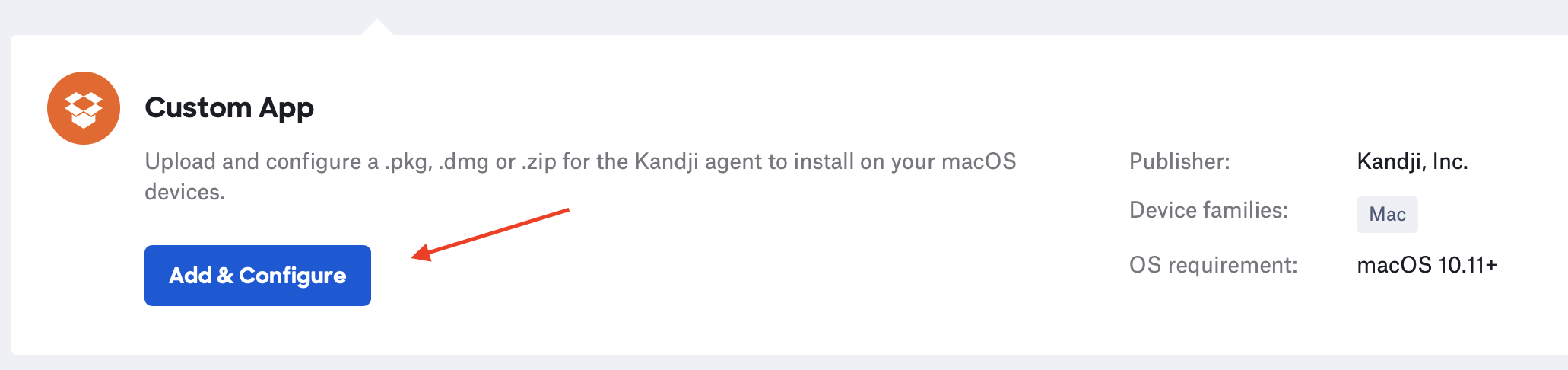
(5) Click the blue “Add & Configure” button
(6) Scroll down to “Install Details” and select the “ZIP File” radio button
(7) In the “Unzip Location” text field enter, “/Library/Application Support/Trusona/”
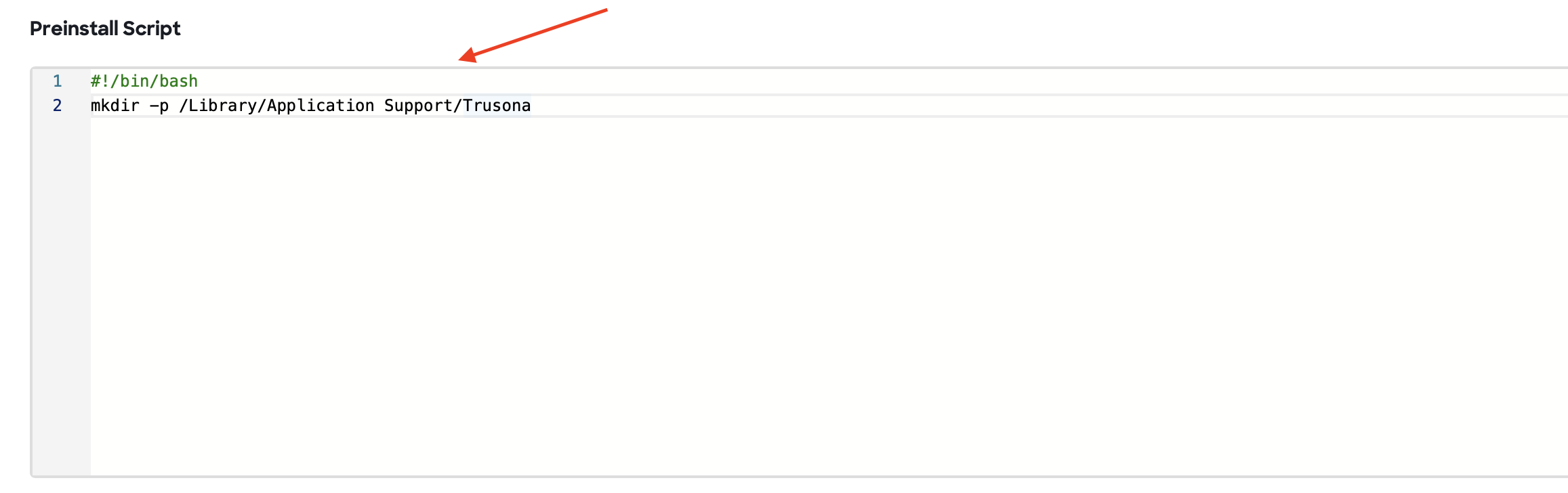
(8) In the “Preinstall Script” text field enter:
#!/bin/bash
mkdir -p "/Library/Application Support/Trusona"
(9) Drag and drop the credential.json file to the upload section under “ZIP File”
(10) Click the blue “Save” button in the bottom right-hand corner
The Trusona application will be installed the next time the machine checks in with Kandji (15 minutes by default). To force a check-in, open Terminal on the target machine and type:
sudo Kandji run
After installation, you will find the Trusona app in the Applications folder.
5. FileVault Considerations
Many enterprise deployments use FileVault which alters the login sequence. This section explains how you can use Multi-Factor authentication with FileVault.
When you Restart or power on your Macintosh, it first boots from a hidden partition called Recovery to show the FileVault 2 pre-boot login screen. Apple cleverly makes this screen look very similar to the macOS login window so many users are not aware that macOS hasn’t started yet.
5.1. Restart with FileVault ON
Upon restart, the pre-boot login screen prompts for your FileVault password to unlock the Startup partition containing macOS. The FileVault password you enter is temporarily saved in the Authorization Context for the next phase.
After macOS starts up it attempts to login using the FileVault password that was saved in the Authorization Context if any. If the login succeeds, you will be logged in automatically so you don’t need to enter your password a second time. In this case the Trusona authorization plugin is not invoked.
To get around FileVault bypassing Trusona authentication, an administrator can disable the autologin feature (DisableFDEAutoLogin). In this case Trusona two factor authentication will be required for macOS login even though FileVault prompted for a password at the pre-boot login screen.
5.2. Restart with FileVault OFF
When FileVault is not enabled, pre-boot unlocks the Startup Disk containing macOS without requiring a password. There is no FileVault password saved in the Authorization Context so macOS will invoke the Trusona authorization plugin to complete the login process.
We hope you enjoy using Trusona for the Mac and are here to help.
- The Trusona team